SCCM - Microsoft's Native C2
A lot of hype has come out around System Center Configuration Manager (SCCM), Microsoft's software management suite that allows administrators
Red Team Operator 2 is the continuation of the educational content and certifications from RastaMouse at Zero Point Security. This builds upon RTO 1 foundations and ramps up the difficulty by throwing AV and EDR into the mix. The goal is to educate users on common and modern tactics to evade defenses while using Cobalt Strike, a commercial Command n Control software from Help Systems.
RTO II is a continuation (not a replacement) of Red Team Ops and aims to build on its foundation. The primary focus of this course is to provide more advanced OPSEC tactics and defence bypass strategies.
Students will:
As I have already taken a majority of the Sektor classes around malware development, the C++ and Windows API content was familiar to me. The introduction of C# content and working with various tools to use this language as well was a great inclusion and will be added to the list of languages to learn. This follows the previous RTO as the designated C2 is a licensed Cobalt Strike instance running via Ubuntu and a development attacking windows box for C# tooling and various offensive/admin windows utilities. The course material is now hosted at https://training.zeropointsecurity.co.uk/. New additions include linux hosts to act as redirectors for C2 traffic as boxes are now firewalled off directly from the teamserver. You will have to be able to setup properly configured beacons and redirectors to achieve successful callbacks. No worries, as this is gone over pretty well and straight forward in the course. The lab is also hosted via Snaplabs as before.
Pretty self explanatory, basic information about the course, how to use the lab, etc.
Learn how to configure Apache redirectors and beacons. This module also covers SSL certificates and keystores for signing generated payloads within cobalt strike. You'll also learn how to modify C2 profiles and some cool tricks to keep your teamserver safe from prying eyes.
Module goes over the basic windows API and how to write skeleton code to achevie simple objects first such as a MessageBox, then moving into some more useful tactics around calling use API functions from C++ and C#. You'll also be introduced to use tools like D/Invoke and how to use Ordinals versus API function names.
Pretty much a continuation of the previous module, except it's all about process injection using various different API functions with skeleton code provided to give you a working sample to build from. Points are given around the OPSEC of each one and why you may use one technique over another depending on the situation.
Exactly as it sounds, this module goes into all things evasive while working with Cobalt Strike. This goes over what happens behind the scenes with various CS functions such as Spawnto, ppid, and pipes. You'll also learn about the Sleep Mask kit, bypassing things such as ETW (Event Tracing for Windows), and memory protections.
This module goes into various aspects of ASR (Attack Surface Reduction), a security rule system enforced by Windows Defender that allows various rules to be enabled that restrict common attack signatures. A sample of these are:
You'll learn how to identify and bypass some of these rules.
This module goes into WDAC, a windows policy tool that can control drivers and applications being executed on a host. You will learn how to find these policies, parse them, and read them in order to identify possible weaknesses in the policy. This may include things like exploiting custom applications, trusted code signers or applications (LOLBAS), and weak application permissions.
The final module goes into detail around EDR's and how they work. You'll go into how they hook applications, detecting the hooks and some bypass strategies. You'll segway into working with direct Syscalls and implementing them into your Cobalt Strike arsenal and custom code templates. Finally this ends with a tease into driver enforcement/exploitation and learning about User Defined Reflective Loaders.
You are free to schedule the exam right after buying the course. There is no limit on retakes but they are charged at £99.00 which is around $131. You are provided a voucher for the exam if you buy the full course package. The exam is allocated 72 runtime hours with 5 days of access from the start of the exam booking date. You are not provided with web access to the exam machines for obvious reasons except the initial compromise vector. Scoring is based on flags in the environment, with a total of 4 possible flags. To pass, you must get all 4 flags submitted in SnapLabs. I initially began my exam on October first, but due to some initial lab and life trouble and a death in the family, I did not complete my exam. I plan on returning to this in the near feature. Completion of this exam rewards the Red Team Lead badge and certification.
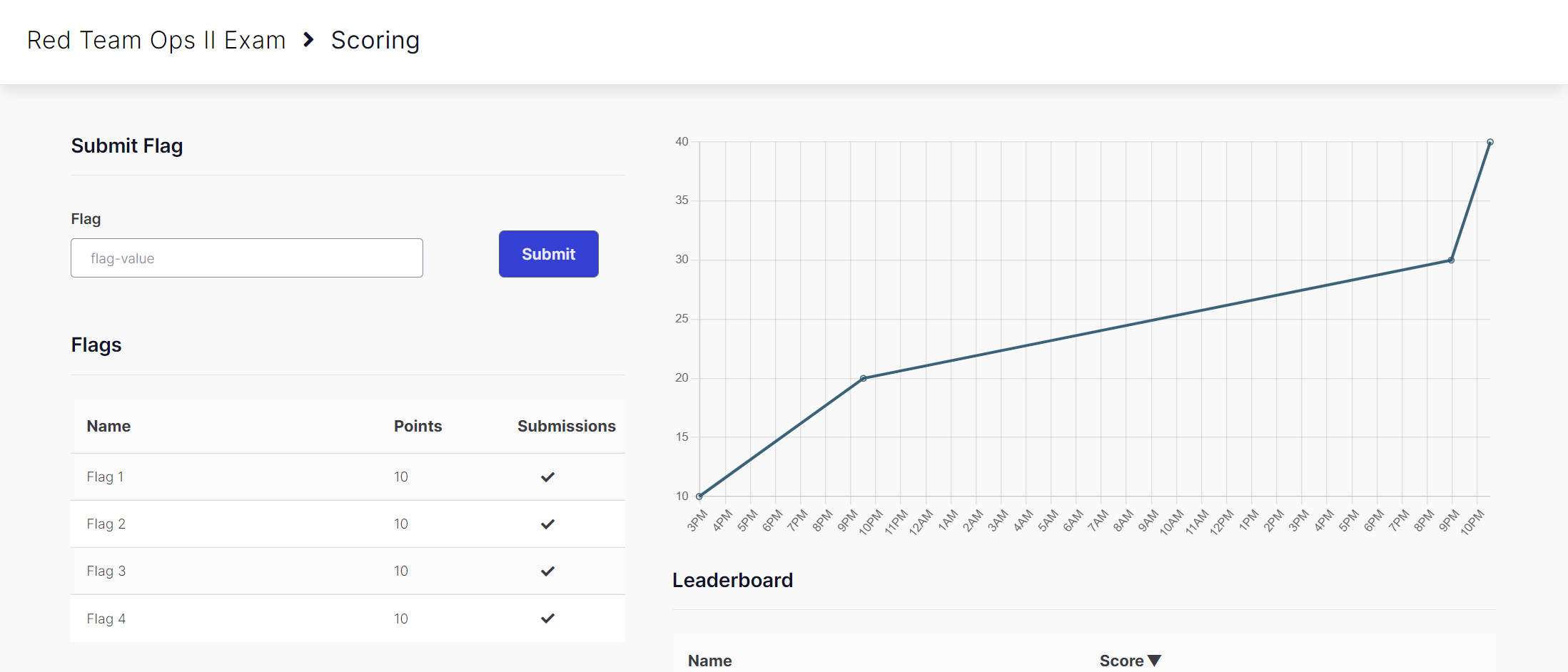
Booking:

Overall I found the course to be fantastic in terms of quality of information, experience gained, and takeaways compared to its price point. Below is a quick list of my pros/cons:
I highly recommend this course for any looking to get a solid grasp on red team evasion tactics and learning techniques to improve the usability of Cobalt Strike in an evasive manner.
