IronSuite - IronEye v2.0 + IronFist Loader Showcase
It's been a while since any big updates but I have not been idle. I'll be showcasing two major tool updates for this article. One is I
Tales of Cybersecurity, Threat Research, CTFs, and Offensive Operations
It's been a while since any big updates but I have not been idle. I'll be showcasing two major tool updates for this article. One is I
Anyone working in IT, particularly in the consulting space loves home labs. Some people dedicate entire closets in their house, even rooms to
It's been a while since any big updates but I have not been idle. I'll be showcasing two major tool updates for this article. One is I
A quick look at Windows Persistence via RegisterApplicationRestart
As an offensive security consultant, I've had my fair share of experience with command and control frameworks. Everything from commercial
Description: A mullti-purpose LDAP tool written in Rust. Created By: Evasive_Ginger
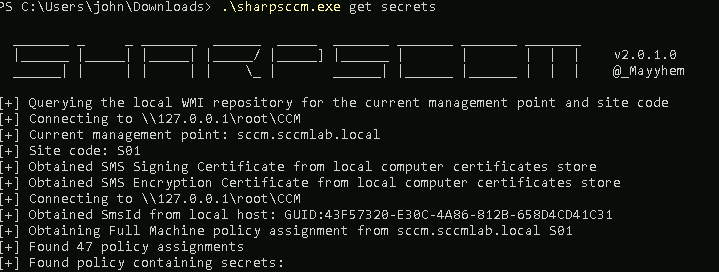
A lot of hype has come out around System Center Configuration Manager (SCCM), Microsoft's software management suite that allows administra
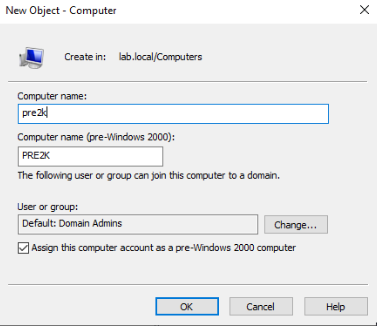
How legacy compatibility options and misconfigured ADCS can lead to a real bad day.